Cyber Security starts with a Cyber Security Assessment: the primary need is to know the current state of a businesses Cyber Security defences, and to understand what assets there are to be protected, not forgetting their valuation.
After all, we need to understand how much effort and cost should be devoted to protecting each asset!
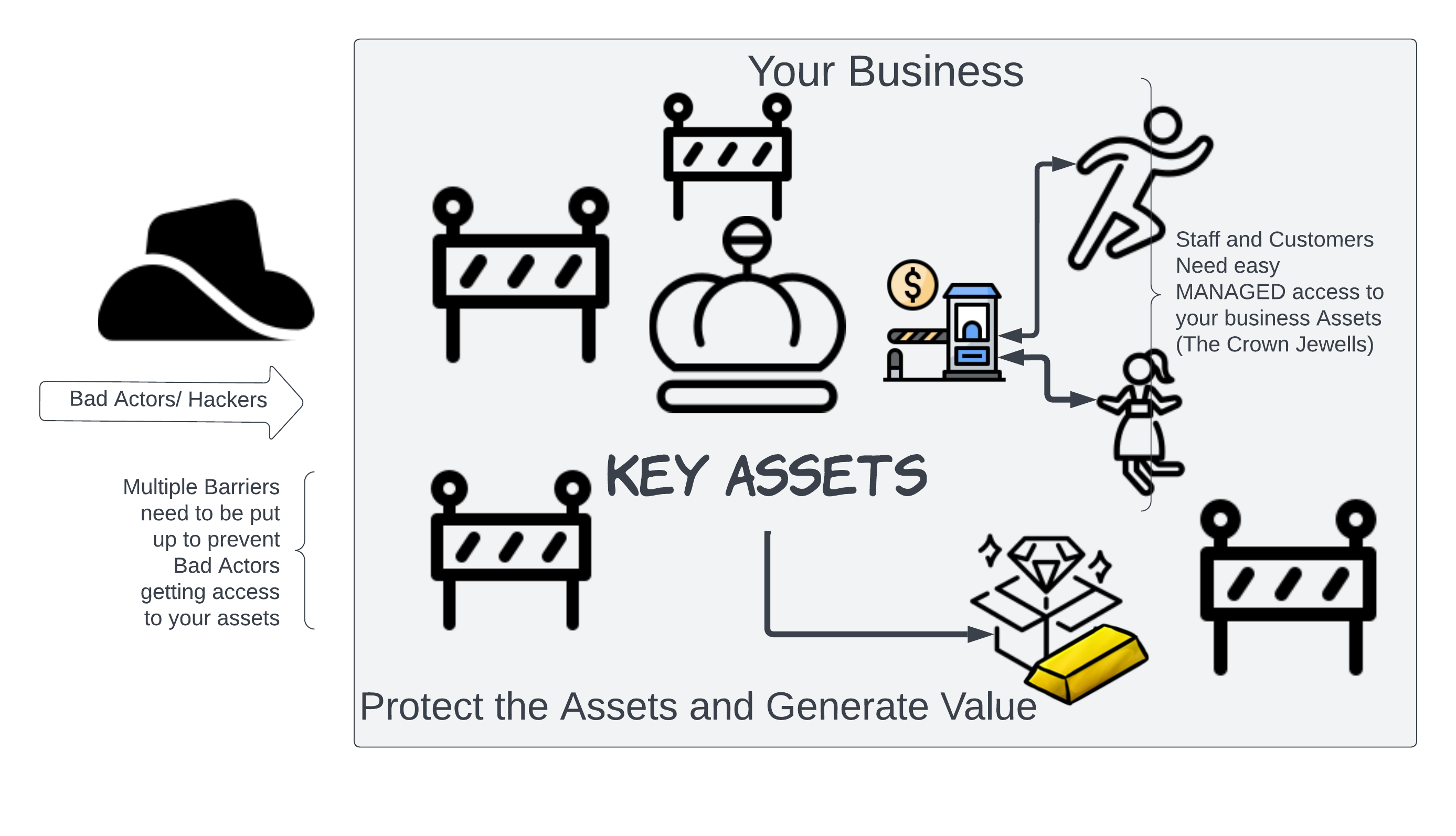
A Cyber Security Assessment is a comprehensive review of an organisation's information security landscape. It identifies vulnerabilities in the systems and helps to understand how these vulnerabilities might be exploited by threat actors. The goal of the assessment is to protect an organisation's information, data, and IT assets.
Talk to us about Cyber Security Assessment
Click the link below to book a FREE meeting where we will explain, in person how we conduct a Cyber Security Assessment.
We will explain what is needed from you and what you can expect as well as the access we will need to your business.
We will also explain what you will get from the study.
We provide Fixed Price Cyber Security Assessment
A Cyber Security Assessment should cover at least the following areas:
- Risk Assessment: Identify and classify potential threats, risks, and vulnerabilities in the organisation's systems and infrastructure.
- Security Policies and Procedures: Review the organisation's information security policies, procedures, and controls. This should include incident response and disaster recovery plans.
- Technical Controls: Evaluate the effectiveness of technical security controls like firewalls, intrusion detection systems, encryption, and anti-virus software.
- Physical Security: Assess the physical security measures such as access control to the data centres, server rooms, and other key areas where sensitive data is stored or processed.
- Network Security: Review of the network architecture, including all devices, connections, protocols, and security measures.
- Application Security: Evaluate security controls for all critical applications, including third-party and internally developed applications. This should also include mobile applications.
- Data Security and Privacy: Evaluate the controls around data privacy and how data is stored, processed, transmitted, and disposed of. This includes assessing compliance with data protection laws and regulations.
- Employee Training and Awareness: Determine whether employees are trained and aware of security threats and best practices. Regular training can help prevent many common threats, such as phishing.
- Vendor Management: Review the organisation's relationships with vendors and third parties. This includes assessing their security controls and their access to your organisation's data and systems.
- Incident Response Plan: Check how prepared the organisation is to respond to security incidents. This includes a review of the incident response plan and its execution.
- Regulatory Compliance: Determine whether the organisation complies with the relevant industry and government regulations and standards like GDPR, ISO 27001, and PCI DSS.
- Patch Management: Review how the organisation is managing and applying patches to its software and systems.
These are just some key areas; a Cyber Security Assessment may cover other aspects based on the specific needs of an organisation. The assessment should result in a set of recommendations to help the organisation improve its security.